Set up your own Ethical Hacking Lab
Learn how to set up your own Lab in a safe, secure environment.
As an IT enthusiast, wouldn't be great to put all our learned skills to practice and see how it plays out in a real-world environment?
A safe and secure environment for ethical hacking is vital, as we don't want to raise any alerts to our Internet Service Provider (ISP) by actively scanning hosts and servers, which is against the law.
Please be aware, hacking person or company without their permission is illegal.
let's create a safe environment with the Virtualisation
- Download and install VirtualBox. This is a free open-source virtual machine hypervisor, that let us run most of the operating system (OS) in an isolated environment. This borrows hardware resources from our physical machine.
2. Whilst VirtualBox is downloading, go ahead and download the Kali Linux virtual machine OS. It's an open source Debian based OS which we will be running on our VirtualBox hypervisor.
Download Kali Linux distribution (distro). This is the most popular Linux distro OS used by Penetration Testers, Security Researchers and Computer Forensics.

Now we have downloaded and installed our VirtualBox which will let us borrow our computer hardware resources as a virtual machine. We have also downloaded our hacking distro Kali to attack our target machine. Our target machine is going to be our vulnerable OS, which is prone to malicious attacks.
3. There are thousands of vulnerable OS to download and practice our hacking skills. We going to search and download Mr-Robot: 1 form search bar at the top.
4. This is an important part where we will secure our lab environment. In other words, we will isolate Kali and Mr-Rbobot:1 OS communicating to the internet, and machine we run hypervisor (VirtualBox)
To do this, we have to modify our network settings in our VirtualBox. Navigate to settings from your Kali Hacking machine, by right-clicking on the setting, networking tap, and Attach to Internal Network from (NAT) Network Address Translation. You can name your network whatever you like. I have named it HackingLab
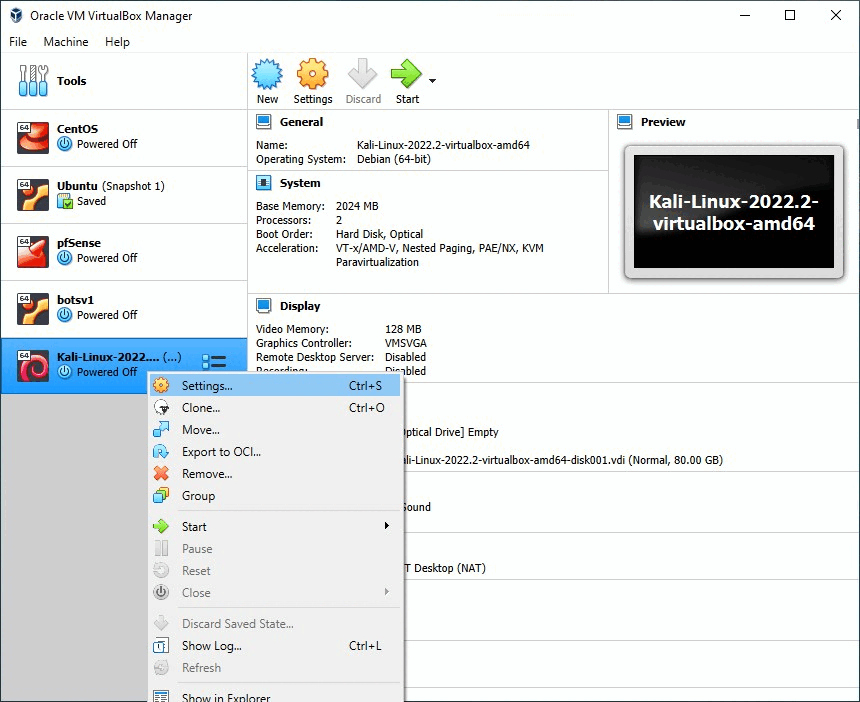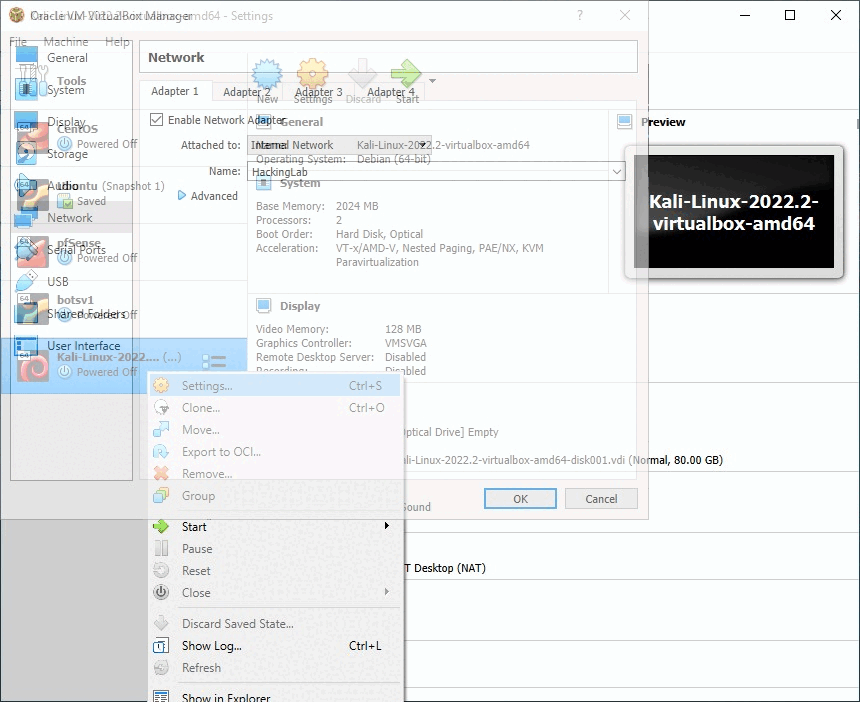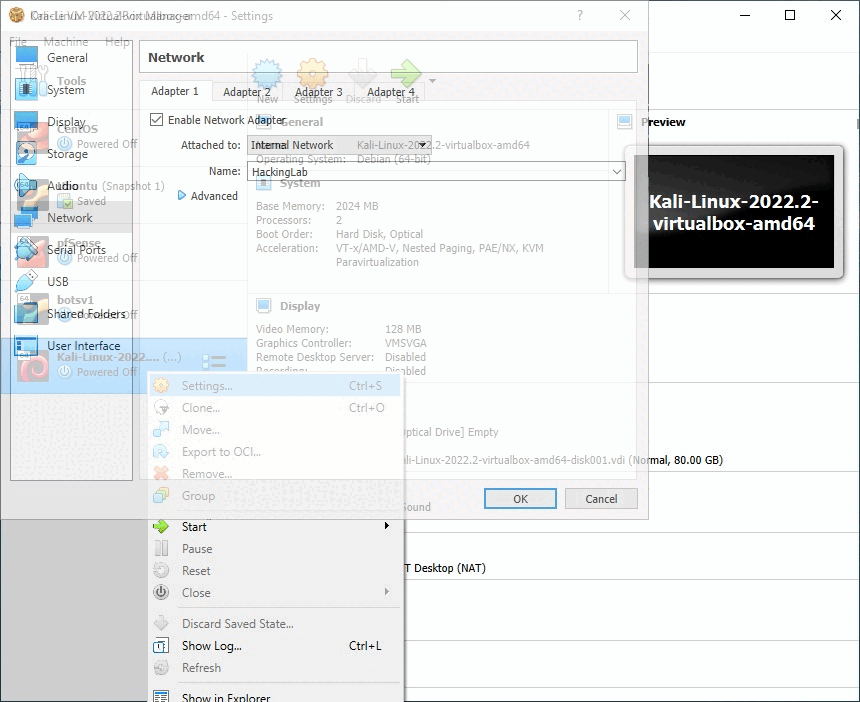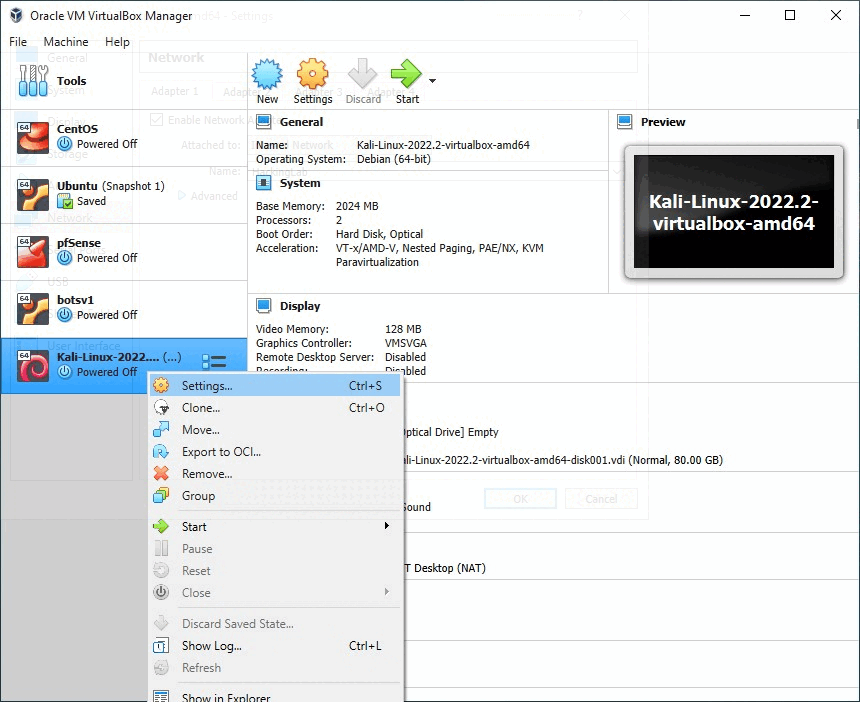
Make sure we set same settings to our vulnerable machine MR-ROBOT: 1 so our both machines can talk to each other on the same network.
5. Create a DHCP Server, this is known as Dynamic Host Configuration Protocol or simply DHCP. Its a network server that automatically provides and assigns IP addresses, default gateways and other network parameters to client devices. This is responsible for ensuring all the devices on the network has IP address assigned.
Both of our operating system will not have an IP Address assigned to them when they bootup, therefore we need to set-up an DHCP server.
Open the Terminal from your window, and type the following command as shown below.
Command Prompt - Output
Microsoft Windows [Version 10.0.19041.804] (c) 2020 Microsoft Corporation. All rights reserved.
C:\Users\Jay>cd /Program Files/Oracle/VirtualBox
C:\Program Files\Oracle\VirtualBox>vboxmanage dhcpserver add --network=HackingLab --server-ip=10.30.1.1 --lower-ip=10.30.1.100 --upper-ip=10.30.1.115 --netmask=255.255.255.0 --enable
a. Command Prompt welcome screen with Windows version and released year
b. The second section of command shows user navigating to VirtualBox file path.
c. Last section is a command using vboxmanage tool, then we are stating the option to add DHCP Server dhcpserver add followed by network name we have created -network=HackingLab. Finally, we tell what IP address range we want DHCP to dish out ,--server-ip=10.30.1.1 --lower-ip=10.30.1.100 --upper-ip=10.30.1.115 --netmask=255.255.255.0 then enable the DHCP server.
Now we have our isolated network that can only be discovered by target machine Mr-Robot: 1 and an attacking machine (Kali). Since we have isolated these two machines on the same network, only these two machines can communicate between each other, and these are not exposed to the internet.
We are ready to practise testing on our newly build Hacking Lab!
Member discussion