How to harden Linux Server like a Pro!
Linux server hardening is the process of securing a Linux-based server by implementing various measures to protect it against potential security threats. Hardening involves minimizing vulnerabilities, reducing attack surface, and implementing robust security controls to ensure the server's integrity, confidentiality, and availability.

Content Table
- Encrypted Communication
- Use SSH Keys instead of Password
- User Account security policy
- Disable root login
- Keep the system updated
- Check for open ports
- Monitoring login access
- Implement IDS
Encrypted Communication
Secure Shell (SSH) provides secure authentication and encryption of data during transmission over the network. It uses a combination of cryptography methods to authenticate users and encrypt data transmitted over the network.
When we establishes an SSH connection to a server, we must authenticate ourself with a username and password or public/private key pair. Once authenticated, the client and server establish a secure encrypted connection, and all data transmitted between them is encrypted and decrypted at each end.
- SSH - Secure Shell
- Change default SSH port 22
- Create SSH key instead of Password
SSH - Secure Connection
Creating a secure encrypted connection to Server as shown below.
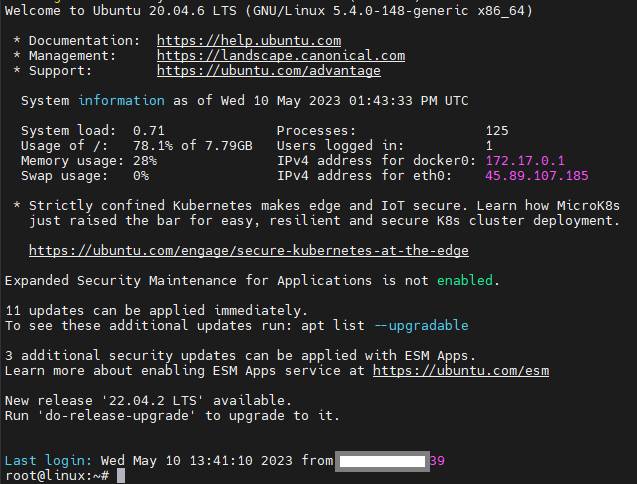
Change default SSH port
The default port to access SSH is 22, which is automatically configured during the operating system installation. However, we can minimise the risk of brute force attacks by changing it to any ports between 1024 and 65536.
- Log into server as Administrator
- Open SSH config file sshd_config using the text editor vi
vi /etc/ssh/sshd_config3. Find the entry for Port 22
4. Replace port 22 with a port between 1024 - 65536
5. Save the file entering :wq on vim
6. Restart the service
Ubuntu
service ssh restartCentOS 7
systemctl restart sshd7. SSH using newly assigned port
ssh root@<Server_IP_address> -P <new_port> cat /etc/services fileCreate SSH key
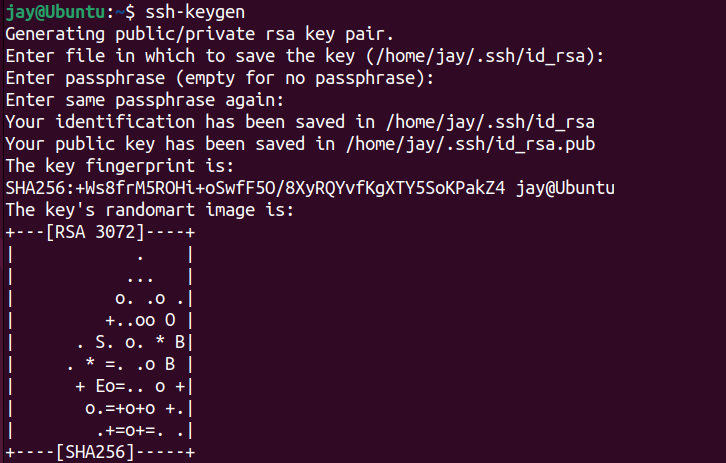
- Generate a public/private key pair on the client device using a following command
ssh-keygen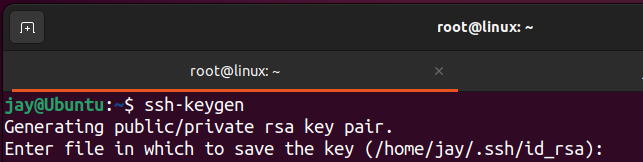
2. Press enter to save the key pair into the .ssh/ subdirectory in our home directory, or specify an alternate path.
3. This is optional. A passphrase adds an additional layer of security to prevent unauthorised users from logging in, it is optional, but recommended for additional layer of security.
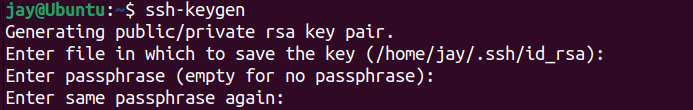
After entering the passphrase, the system will generate public and private key that we can use to authenticate.
4. Copy Public key to Server
When generating an SSH key pair, a public key and a private key are created. The private key should be kept securely on your local host, while the public key can be shared with remote servers that we want to authenticate with. By transferring the public key to the server, we can authenticate with the private key and establish a secure connection without having to enter a password.
The ssh-copy-id tool is included by default in many Linux operating system. Copy the public key to the server using the ssh-copy-id tool command or manually adding it to the authorised_keys file on the server.
Enter the command
ssh-copy-id -i ~/.ssh/id_rsa.pub root@<Server_IP_Address>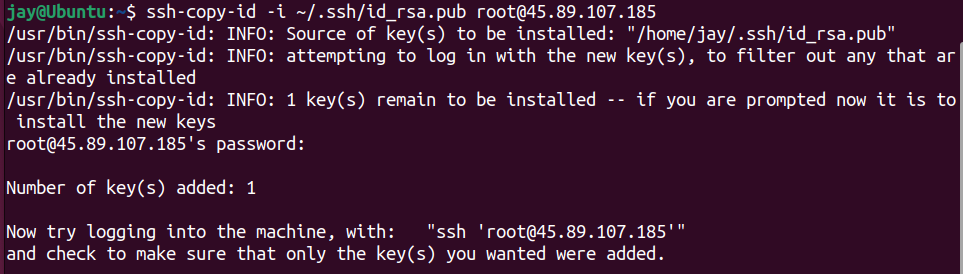
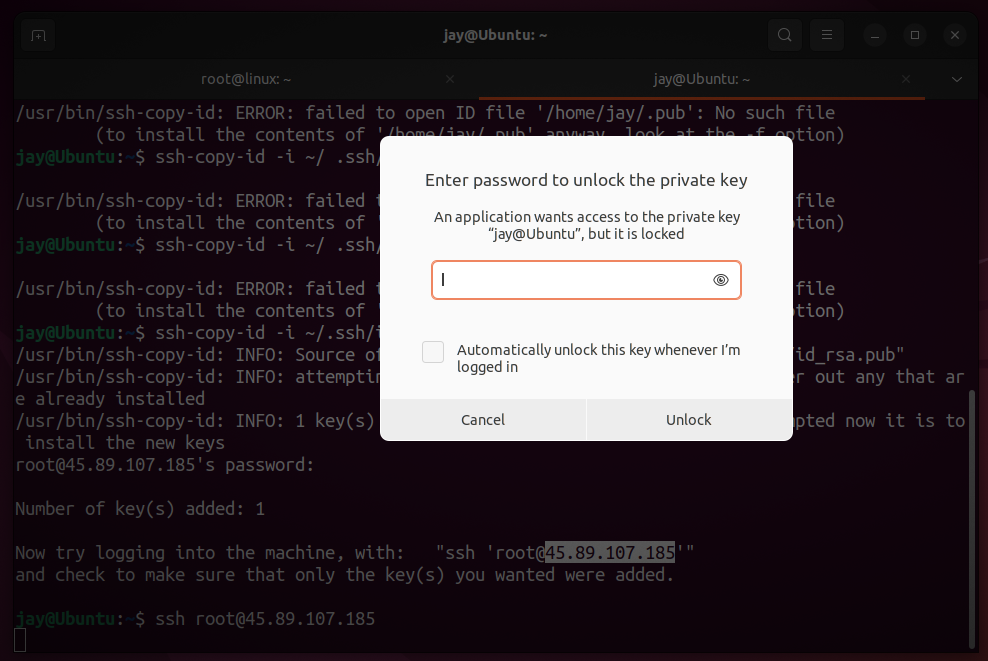
One we try to log into the server, we will be prompt with Passphrase which we have set up at the beginning. Enter the passphrase to connect.
5. Disable the Password Authentication
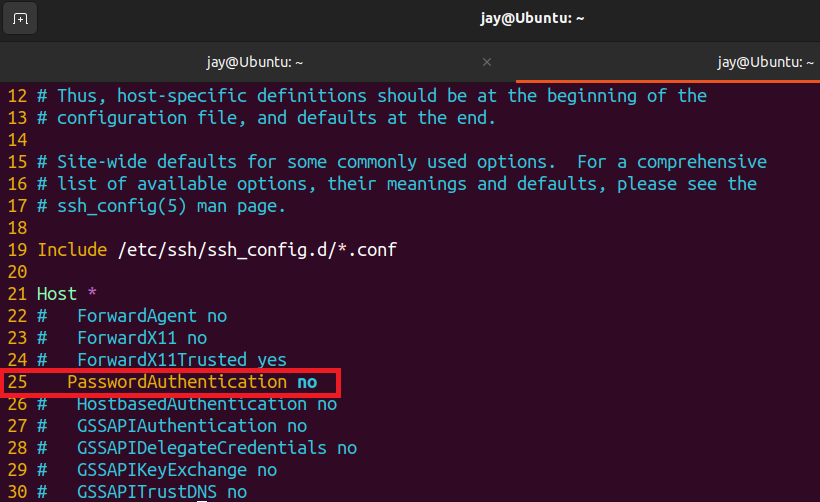
Once we have set up SSH Key authentication, we can disable the password log in by changing the sshd_config file using Vim text editor
vim /etc/ssh/sshd_configFind the line that starts with PasswordAuthentication , then change the value from yes to no. If the line is commented out with a # symbol, remove the symbol. then save the file by entering :wq
6. Restart the SSH Service to apply the changes.
sudo systemctl restart sshdOnce password authentication is disabled, users will only be able to authenticate using SSH keys. This provides a more secure method of authentication, as it prevents brute-force attacks that attempt to guess passwords. However, it is important to make sure that your SSH keys are secure and kept in a safe location.
User account security policy
One of the common security practices on any Linux machines is to avoid using the root account for day to day operations. If we have just deployed a new cloud server, the only account on it will be root, so we will need to create a new username for ourself.
Enter the following command to create a new user
adduser <username>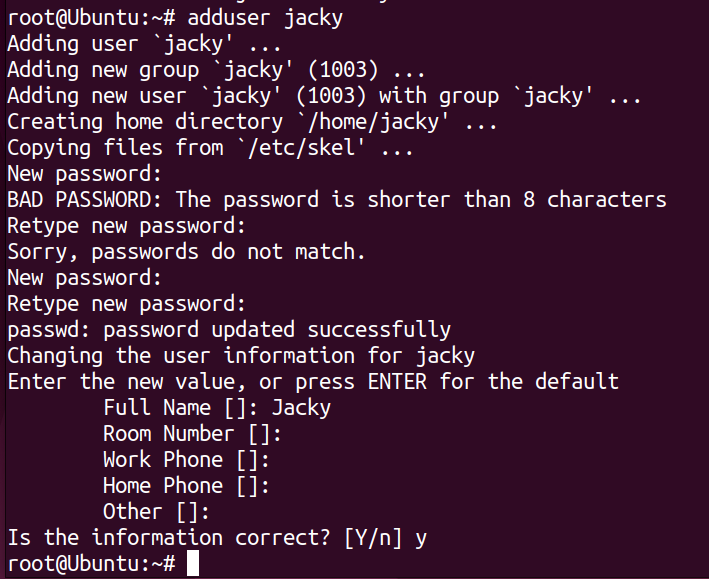
If we want to use this account for Admin, we need to give this user a sudo (super user do) execution privilege. We can do this by following command.
adduser <username> sudo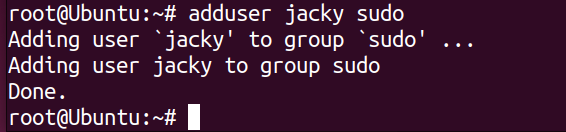
Adding sudo permission to Cent OS is a little different. Use the following command for Cent OS
gpasswd -a <username> wheelOn Debian, sudo access control system may not be installed by default. If it is not there, use the following command to install.
apt-get install sudoOnce installed, user the same command as with Ubuntu, as covered earlier.
By granting sudo permissions, we can perform the same tasks as the root account while maintaining security. It's safer to give other users on our server sudo privileges instead of sharing the root password. Using sudo is commonly recommended for better security practices.
Disable root login
We should disable SSH remote login for root, once we have our own account set up. The OpenSSH server settings are defined in a configuration file, open it in Vim editor on Debian or Ubuntu using the command below.
sudo vim /etc/ssh/sshd_configFind the authentication options and change the root permission by changing it to no as shown below.
PermitRootLogin noOnce change has been made, exit the file.
Restart the SSH server as shown below.
systemctl restart sshdUpdate your system
Its essential to regularly monitor our Linux server for updates to promptly address new vulnerabilities and apply necessary patches. Also, our cloud server is equipped with the latest fixes to maintain system security and keep it up to date.
sudo apt-get update && sudo apt-get upgradeThis is the simple method to update the packages already installed on your server
sudo apt-get update && sudo apt-get dist-upgradeThe command examines package relationships and prioritises upgrading critical packages over less important ones when needed.
CentOS servers can be updated using the command below.
sudo yum updateYum includes upgrade command, but it might also remove some packages that are obsolete even if we're using them, therefore update command is generally safer.
Check for unused open ports
We will use the Network Mapper (Nmap) tool to scan our network for any unnecessary open ports. This can be installed by following command.
Sudo apt-get install nmapCentOS
sudo yum install nmapScan the localhost using the command below
nmap -v -sT localhostThe result will print out port numbers and services associated with them that are currently open for local connections. We will use the same command to test our server's public IP address.
nmap -v -sT <public IP>An output of public facing server should show similar to screenshot below.
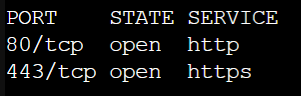
If there are any unrecognised open ports in our server, make sure to disable it.
Monitoring login Access
Once the server is online, it is essentially open to world wide web to accessed by anyone, therefore it is critical to ensure our server is fully patched and secured from malicious attacks.
We might have number of failed login attempts from IP Address other than our own. Majority of the Linux distro keeps logs for authentication from the moment server booted up for the first time.
Different system might store the logs under different names. We can view our Ubuntu or Debian based server logs using the command below.
cat /var/log/auth.log | grep 'ssh.*Invalid'CentOS or Red Hat distro command
cat /var/log/secure | grep 'ssh.*Invalid'Sample output
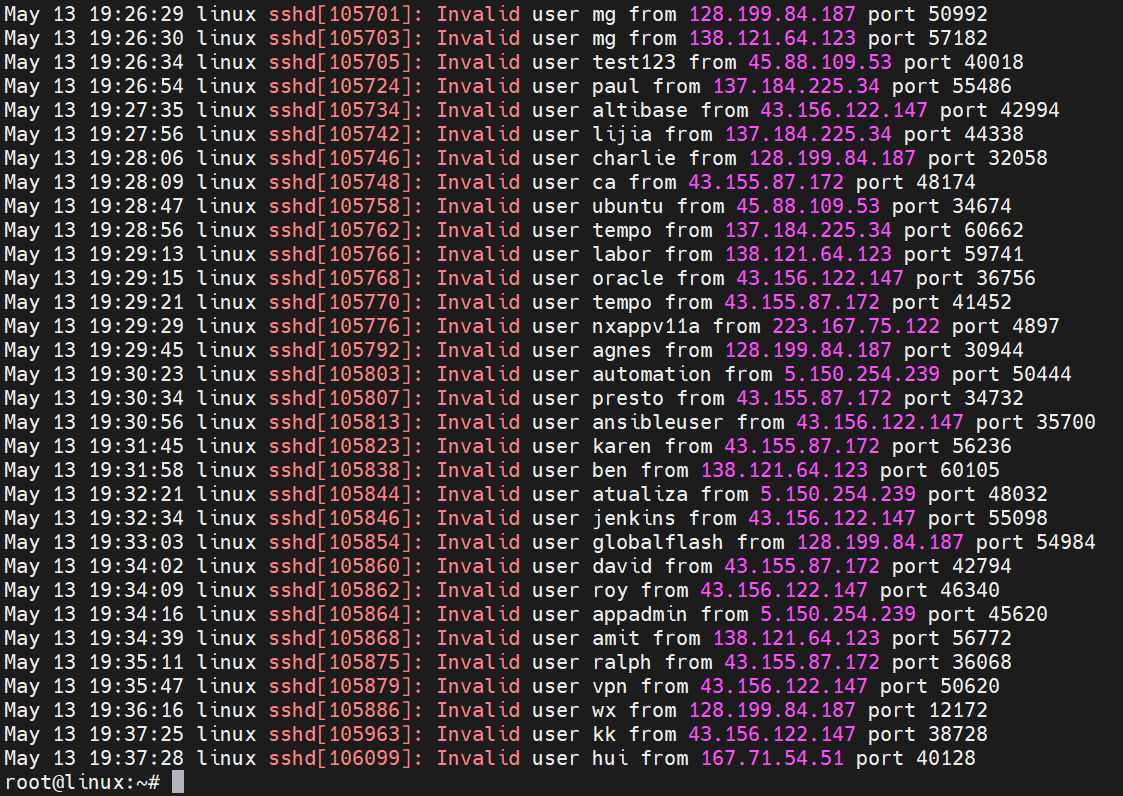
As we can see the output will list dates and times of when invalid login attempts occurred, along with user account used, and IP addresses the connection came from.
There are large number of failed logins attempts, this is just to show how common practice this kind of brute force attempts.
In contract, we can check the logs of successful log in times using the command below.
last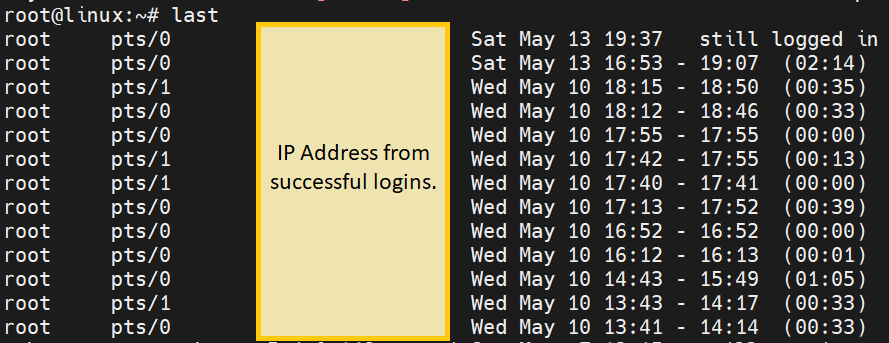
Implement Intrusion Detection System
NIDS
Snort, an open-source, actively developed, and lightweight network-based intrusion detection system (NIDS), is widely preferred and can be installed on even the most compact cloud servers. Check out our guide for installing Snort which we have covered on previous post here.
HIDS
Alternatively, we have host-based intrusion detection system, that performs log analysis, file integrity, policy monitoring, rootkit detection, real-time alerting and active responses.
The main difference between NIDS and HIDS is scope and focus.
HIDS focus on network level and monitors network traffic to detect and respond to intrusions and malicious activities targeting multiple hosts within a network. Whereas, HIDS operates at the host level and focuses on monitoring the activities and integrity of an individual host or endpoint.
Both NIDS and HIDS are important components of a comprehensive security strategy and can be used together to provide layered protection for a network and its individual hosts.
In future post, we will be looking at installation of HIDS and how we can configure and fine tune.
Member discussion