Introduction to Snort
Free open-source IDS/IPS
Snort is a powerful open-source intrusion detection system (IDS) and intrusion prevention system (IPS) that provides real-time network traffic analysis and data packet logging. Snort developed in 1998 and it has been in active development community with thousands of users contributing to keep the Snort up to date to prevent the latest attacks.

Before go any further, let's look at what are the difference between Firewall and IPS
Firewall is a network security device that filters incoming and outgoing network traffic based on predetermined rules, whereas IPS is a device that inspects traffic, detects it, classifies and then proactively stops malicious traffic from attack.
Snort works on library packet capture (Libcap). Libpcap tool is widely used in TCP/IP address traffic sniffers, and content searching, analysing, logging, and content matching.
These are the features of Snort
- Real-time Traffic Monitor
- Packet Logging
- Analysis of Protocol
- Content Matching
- OS Fingerprinting
- Supported on any Network Environment
- Open source
- Rules are easy to implement
Snort has 3 main modes
- Packet Sniffer (Similar to tcp dump)
- Packet Logger (network troubleshooting)
- Intrusion Detection System & Intrusion Prevention System (IDS/ IPS)
Snort detects malicious terrific or attacks by leveraging pattern matching. When active, Snort captures packets, reassembles, analyse and then determines what needs to be done with the packets based on predefined rules. We can think of these rules as similar to firewall rules, that set to prevent certain connection, similarly Snort rules match network activity against specific patterns or signatures and make a decision to send an alert or drop the traffic.
What is the difference between IDS and IPS
As name suggest Intrusion Detection System (IDS) only detects the threats that are coming into the network, whereas Intrusion Prevention System (IPS) detects and threats and prevent it from coming into the network. Some companies have implemented both of the system to protect their network from hackers.
| IDS | IPS | |
|---|---|---|
| Name | Intrusion Detection System | Intrusion Prevention System |
| Description | A system that monitors network traffic for suspicious activity and alerts users | A system that monitors network traffic and alerts for suspicious activity, like an IDS, and also takes preventive action against suspicious activity |
| Location | A host intrucion detection system in installed on the client computer. A network based intrusion detection system resides on the network. | Located between a company's firewall and the rest of its networks. |
| Use | Warn of suspicious activity taking place, but does not prevent it. | Warns of suspicious activity taking place and prevents it |
| False Positive | IDS false positives are usually just a minor inconvenience for Network Engineers, however IDS does not prevent the traffice entering the network | IPS false positive can prevent an organisation from receiving legitimate traffic, that is not a threat. This can impact any organisation. |
Snort has large amount of rule-sets created by the community, and it has been continuously been updated.
There are 3 types of rule sets available in Snort
| Types of Rule-Sets | |
|---|---|
| Community Rules | Free rule-sets created by the Snort Community |
| Registered Rules | Free Rule-sest created by Cisco Talos. In order to user the, we need to register |
| Subscription Rules | These rules requires an active paid subscription to use them |
Alternatively, we can create a new rules based on our requirements. The following diagram shows the Snort rule syntax explains each aspect of the Snort rule.
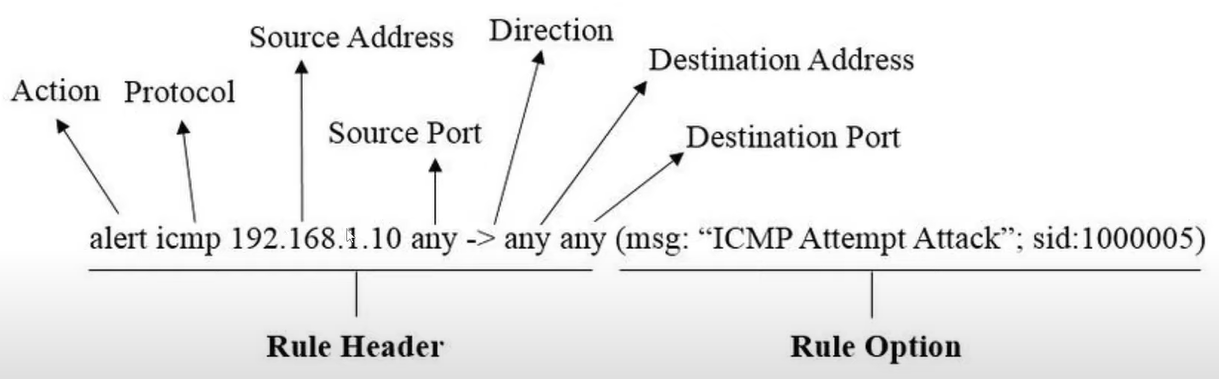
How Snort Works
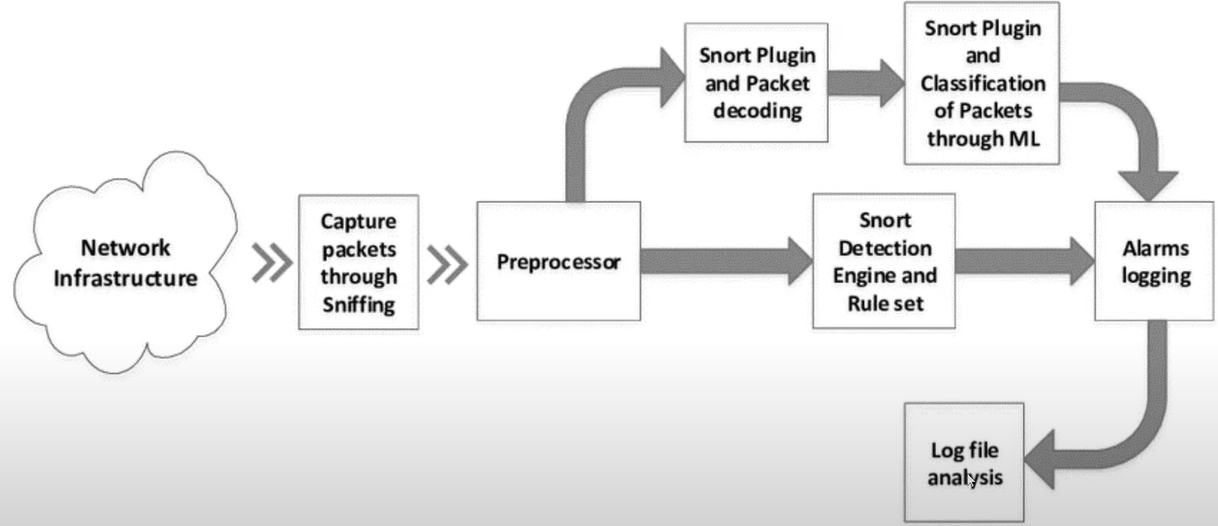
Network Placement of Snort
Snort has two modes. It can either function has IDS or IPS.
The following diagram shows placing a Snort between firewall and switch will gives Snort to analyse all the inbound traffics from the Firewall, which has been already filtered by firewall, giving Snort less packs to efficiently analyse and action.
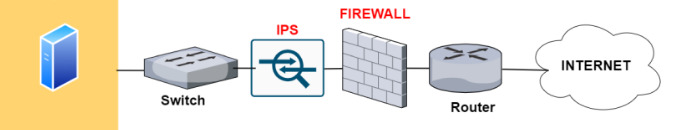
We have looked at IPS in previous diagram, where the rules are actioned based on the threat that matches the rules.
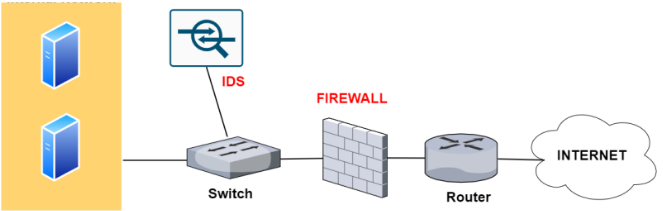
In IDS, Snort is placed in subnet of other machines where It can monitor all the intrusions and threats that are detected from switch, but as we know, it would not prevent the traffic.
Summary
Snort is a free open source IDS/IPS, that let you scan and analyse your packets in your home or cooperate network. We will be covering how Snort can be installed and configured on our next post.
Member discussion