Introduction to Splunk - (SIEM Tool)
Splunk is a software platform used for collecting, indexing, searching, and analysing machine-generated data in real-time. It enables users to gain insights into their data and gain operational intelligence across their IT, security, and business environments.
Its a SIEM Tool - Security Information and Event Management. It is a software tool that collects, correlates, and analyses security-related information from various sources within an organization's network, such as network devices, servers, applications, and endpoints.
SIEM tools provide real-time visibility into security events occurring across an organization's IT infrastructure. They use a combination of log management, event management, and security information management to identify potential security threats, such as intrusion attempts, malware infections, and insider attacks.
Splunk is a software platform to search, analyse and visualize the machine-generated data gathered from the websites, applications, sensors, devices etc. which make up your IT infrastructure and business.

Splunk is extremely powerful platform that is used to analyse data and logs produced by system. This allows to monitor, search and analyse machine generated data and logs through a web interface. Its like a Google for all our machine data.
All our system generate data based on activities that takes places within the system, these are logged in log files used for investigating error message, debugging, and troubleshooting the system performance.
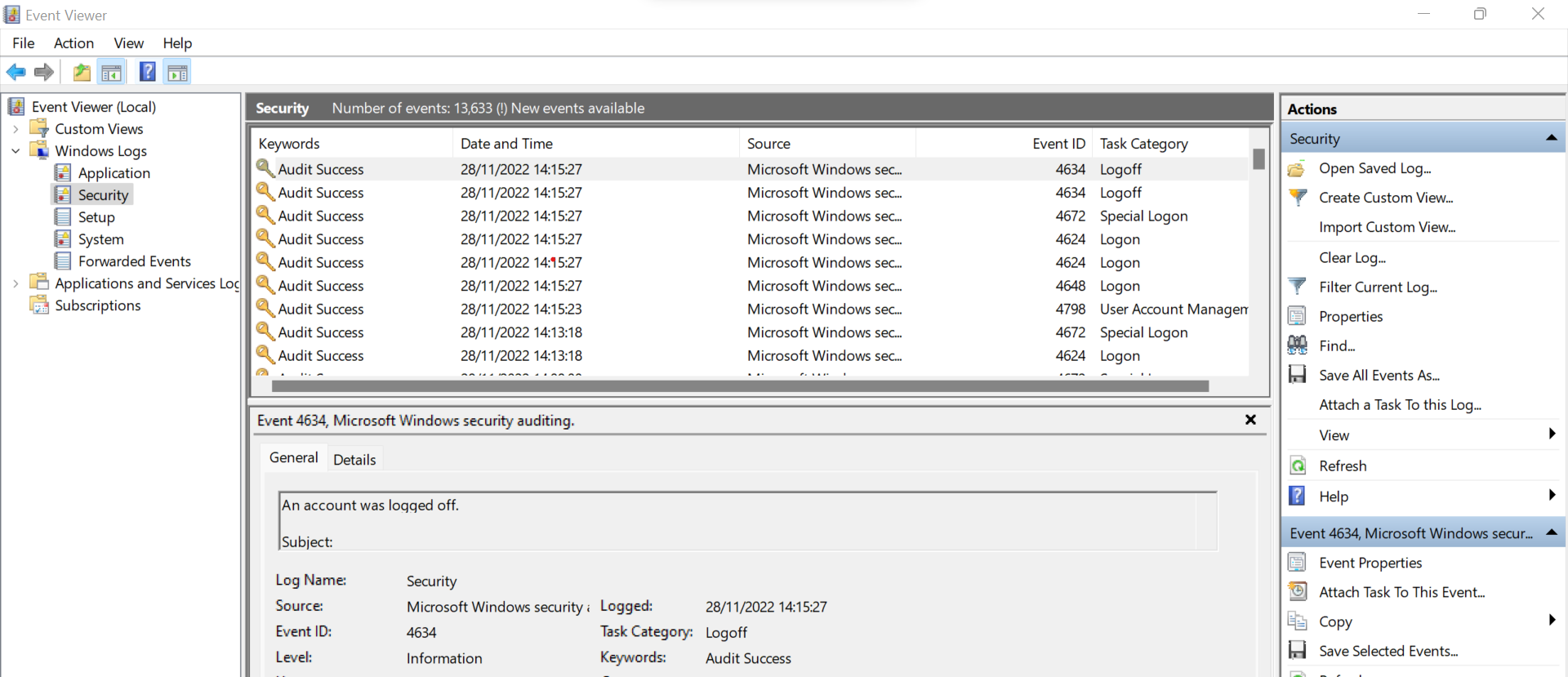
A log file is a computer generated data file that contains information about usage patterns, activities, and operations in operating system. Windows has its logged accessible in Event Viewer
In Linux OS, it has a special directory for storing logs in /var/log/. This directory contains logs from Linux, and various other applications running on the system.
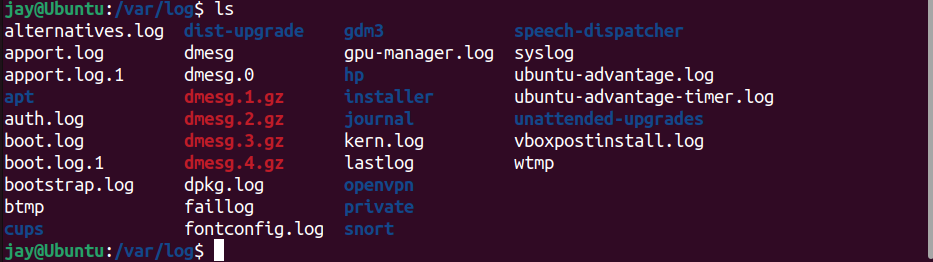
var/log/ directory in LinuxLog files contain valuable information that provides insight into overall system performance on network, software & hardware and other connected devices for any system malfunctions and errors. These are raw data generated by machines.
Splunk collects raw data generated from the machines, then process it to make it human readable to search and find any particular data based on provided information, Splunk has design a search method called Search Processing Language (SPL).
Splunk Comprise of three components, these are as follows
- Forwarder Collect data and forward it to other Splunk instance
- Indexers Where data is stored
- Search Head Analyse, visualise and report the data.
Splunk helps to leverage the machine data into useful insights for better visuals through graphs, charts and other metrics that helps to make critical decisions.
- System Performance
- Failure Conditions
- Business Matrix
- Search and Investigate
- Data Visualisation
- Storing archive data
- Marketing and Sales
There are number of Splunk versions depending on customer requirements, we will be looking at Splunk Enterprise Security (Splunk ES) in more details.
Splunk ES includes Security Information and Event Management (SIEM) solution. It helps us to aggregate unstructured data to achieve visibility into security intelligence across the organisation. It provides simplified threat management that facilitates quick threat detection and response to minimize risks.
Splunk ES help us to manage and run our Security Operation Centre (SOC) as it comes with pre-defined dashboards, metrics, statistics and other Use Case Library to facilitate quicker detection of known and unknown threats.
Use Cassese are varies depending on the customers requirements. In terms of Cyber Security we have the followings.
- Continuous Monitor Security Posture
- Prioritise and Act on Incidents
- Rapid Investigations
- Handle Multi-Step Investigations
Splunk Enterprise Security Features
- Secuirty Posture
- Incident Review and Calssification
- End point Protection
- Network Protection
- Threat Intelligence Frameworks
- Risk Based Analysis
Splunk Overview
We have looked at the existence of Splunk and how it helps to harvest the machine data into invaluable information to make critical decision based on data. In the next article, we will be looking at how to install Splunk on Ubuntu Server.
Member discussion